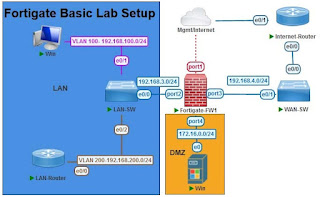
Fortigate Basic Lab Setup in eve-ng/Pnet-Lab
I am two Vlans in LAN and MGMT and Internet traffic is in the same lab
IP details
- Vlan 100 - 192.168.100.1/24
- Vlan 200 - 192.168.200.1/24
- Fortigate-FW1 Port1 - Management port - 192.168.47.10/24
- Fortigate-FW1 Port2 - Data Port - 192.168.3.1/24
- Fortigate-FW1 Port3 - Data Port - 192.168.4.1/24
- Fortigate-FW1 Port4 - Data Port -172.16.0.1/24
- Internet-Router - Eth0/0 - 192.168.4.2/24
- Internet-Router - Eth0/1 - 192.168.47.11/24
- Win Lan-PC - 192.168.100.2/24
- Win DMZ-PC - 172.16.0.2/24
config firewall address
Table of Content
- Prerequisites
- Firewall Introduction
- Where to download the FortiGate Virtual Firewall image?
- Configure Virtual network interfaces for FortiGate
- Deployment of FortiGate VM image in VMWare
- Configuring the lab devices
- Accessing FortiGate Firewall GUI
- Configuration all devices
- Configuring other data ports on the FortiGate
- Configure routing on the fortigate and Policy to allow traffic from LAN to internet
- Testing the traffic flow
- How to take fortigate backup?
Prerequisites: -
- Computer having 16GB of RAM, Minimum i5 Processor
- Vmware workstation
Below are the virtual images I am using in the lab
- Fortinet-FGT-7.0.3
- i86bi_linux_l2-adventerprisek9-ms.SSA.high_iron_20190423.bin
- L3-ADVENTERPRISEK9-M-15.4-2T.bin
Firewall Introduction: -
Fortigate is a Firewall product from Fortinet. Fortigate is a hardware or software-based solution. In this lab, we are using virtual images in PnetLab.
Where to download the FortiGate Virtual Firewall image?
The virtual FW image can be downloaded from the official site or any third-party site
Deployment of FortiGate VM image in VMWare
- Upload all the images in VMware and start the PnetLab. Watch my youtube channel to learn how to upload virtual images in Eve-ng and PnetLab.
Configuring the lab devices
at first, I will configure the FortiGate management interface and access it via SSH and Web-UI
Forti OS reference commands
FortiOS Administration-guide
if you are not sure about the commands on FortiOS you can follow the command reference guide.
FortiGate-VM64-KVM login: admin
Password:
You are forced to change your password. Please input a new password.
New Password:
Confirm Password:
New password must not be the same as the old password.
New Password:
Confirm Password:
Welcome!
FortiGate-VM64-KVM #
- Fortigate virtual machine comes with 15 days trial version which has some limitations
- Verify the status of FortiGate by putting the below command
FortiGate-VM64-KVM # get system status
Version: FortiGate-VM64-KVM v7.0.3,build0237,211207 (GA)
Virus-DB: 1.00000(2018-04-09 18:07)
Extended DB: 1.00000(2018-04-09 18:07)
Extreme DB: 1.00000(2018-04-09 18:07)
AV AI/ML Model: 0.00000(2001-01-01 00:00)
IPS-DB: 6.00741(2015-12-01 02:30)
IPS-ETDB: 6.00741(2015-12-01 02:30)
APP-DB: 6.00741(2015-12-01 02:30)
INDUSTRIAL-DB: 6.00741(2015-12-01 02:30)
IPS Malicious URL Database: 1.00001(2015-01-01 01:01)
Serial-Number: FGVMEVRDGSJCYOFD
License Status: Valid
Evaluation License Expires: Wed May 24 07:52:41 2023
VM Resources: 1 CPU/1 allowed, 997 MB RAM/2048 MB allowed
Log hard disk: Not available
Hostname: FortiGate-VM64-KVM
Operation Mode: NAT
Current virtual domain: root
Max number of virtual domains: 1
Virtual domains status: 1 in NAT mode, 0 in TP mode
Virtual domain configuration: disable
FIPS-CC mode: disable
Current HA mode: standalone
Branch point: 0237
Release Version Information: GA
FortiOS x86-64: Yes
System time: Tue May 9 09:58:06 2023
Last reboot reason: power cycle
- As you see above FortiGate is having one VDOM "root" and the default FW mode is NAT
- port1 is configured as a management interface but we will configure it according to our requirement
- port1 is configured as a management interface but we will configure it according to our requirement
- Allowing https, ssh, ping fgm access on port1
FortiGate-VM64-KVM # config system interface
FortiGate-VM64-KVM (interface) # edit port1
FortiGate-VM64-KVM (port1) # set mode static
FortiGate-VM64-KVM (port1) # set ip 192.168.47.10 255.255.255.0
FortiGate-VM64-KVM (port1) # set allowaccess http https ssh ping fgfm
FortiGate-VM64-KVM (port1) # set description MGMT-PORT
FortiGate-VM64-KVM (port1) # end
Verify the configured interface
FortiGate-VM64-KVM # show system interface
config system interface
edit "port1"
set vdom "root"
set mode static
set ip 192.168.47.10 255.255.255.0
set allowaccess ping https ssh http fgfm
set type physical
set description "MGMT-PORT"
next
end
- Fortigate will automatically save the config once you come out of the config mode
- I will ping my management PC from the firewall
Fortigate-FW # execute ping 192.168.47.2
PING 192.168.47.2 (192.168.47.2): 56 data bytes
64 bytes from 192.168.47.2: icmp_seq=0 ttl=128 time=0.9 ms
64 bytes from 192.168.47.2: icmp_seq=1 ttl=128 time=0.5 ms
As you can see I can access the FW via HTTPS from my management PC. Once you enter the credential, It starts a wizard to configure basic settings
Now our Fortigate is accessible and trust me FortiGate GUI is very easy to navigate.
- Configuration all devices
======================================
LAN-SW
======================================
enable
config t
!
hostname LAN-SW
!
no ip domain-lookup
!
vlan100
name MARKETING
!
vlan 200
name SALES
!
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface Ethernet0/1
switchport access vlan 100
spanning-tree portfast edge
!
interface Ethernet0/2
switchport access vlan 200
duplex full
spanning-tree portfast edge
!
interface Ethernet0/0
no switchport
ip address 192.168.3.2 255.255.255.0
end
!
interface Vlan100
ip address 192.168.100.1 255.255.255.0
no shut
!
interface Vlan200
ip address 192.168.200.1 255.255.255.0
no shut
!
ip routing
!
ip route 0.0.0.0 0.0.0.0 192.168.3.1
!
end
write
=========================================
WAN-SW#
=========================================
enable
config t
!
hostname WAN-SW
!
end
write
!
==========================================
Internet-Router
==========================================
enable
config t
!
hostname Internet-Router
!
interface Ethernet0/0
ip address 192.168.4.2 255.255.255.0
ip nat inside
!
interface Ethernet0/1
ip address 192.168.47.11 255.255.255.0
ip nat outside
!
access-list 1 permit any
ip nat inside source list 1 interface Ethernet0/1 overload
ip route 0.0.0.0 0.0.0.0 192.168.47.2 name INTERNET-NEXT-HOP
!
ip route 192.168.100.0 255.255.255.0 192.168.4.1
ip route 192.168.200.0 255.255.255.0 192.168.4.1
!
end
write
!
Internet-Router#ping 192.168.47.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.47.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Internet-Router#
====================================
LAN-ROUTER
====================================
enable
config t
!
hostname LAN-ROUTER
!
interface Ethernet0/0
ip address 192.168.200.2 255.255.255.0
no shutdown
!
ip route 0.0.0.0 0.0.0.0 192.168.200.1
!
end
write
!
LAN-ROUTER#ping 192.168.200.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
LAN-ROUTER#
!
======================================
LAN-WIN-PC
======================================
- Assign an IP address - 192.168.3.2 255.255.255.0 and default-gateway 192.168.100.1
- Ping 192.168.3.1
======================================
======================================
DMZ-WIN-PC
======================================
- Assign an IP address - 172.16.0.2 255.255.255.0 and default-gateway 172.16.0.1
- Ping 172.16.0.1
======================================
- Now we will configure other interfaces and routing on the FW to reach the internet
- Configuring other data ports on the FortiGate
config system interface
edit "port2"
set vdom "root"
set mode static
set ip 192.168.3.1 255.255.255.0
set allowaccess ping
set type physical
set description "LAN-TRUST-PORT"
next
edit "port3"
set vdom "root"
set mode static
set ip 192.168.4.1 255.255.255.0
set allowaccess ping
set type physical
set description "LAN-UNTRUST-PORT"
next
edit "port4"
set vdom "root"
set mode static
set ip 172.16.0.1 255.255.255.0
set allowaccess ping
set type physical
set description "DMZ-TRUST-PORT"
next
end
- Pinging all directly connected devices from the Fortigate
Fortigate-FW # execute ping 192.168.3.2
PING 192.168.3.2 (192.168.3.2): 56 data bytes
64 bytes from 192.168.3.2: icmp_seq=0 ttl=255 time=1.1 ms
64 bytes from 192.168.3.2: icmp_seq=1 ttl=255 time=0.7 ms
Fortigate-FW # execute ping 192.168.4.2
PING 192.168.4.2 (192.168.4.2): 56 data bytes
64 bytes from 192.168.4.2: icmp_seq=1 ttl=255 time=1.6 ms
64 bytes from 192.168.4.2: icmp_seq=2 ttl=255 time=1.3 ms
Fortigate-FW # execute ping 172.16.0.2
PING 172.16.0.2 (172.16.0.2): 56 data bytes
64 bytes from 172.16.0.2: icmp_seq=0 ttl=128 time=4.8 ms
64 bytes from 172.16.0.2: icmp_seq=1 ttl=128 time=312.7 ms
- Configure routing on the fortigate and Policy to allow traffic from LAN to internet
- Configuring a default route towards internet router to reach the internet
config router static
edit 1
set gateway 192.168.4.2
set device "port3"
set comment "TO_Internet_TRAFFIC"
next
- Configuring static route for vlan 100 and vlan 200 reachability
config router static
edit 2
set dst 192.168.100.0 255.255.255.0
set gateway 192.168.3.2
set device "port2"
set comment "TO_VLAN100"
next
edit 3
set dst 192.168.200.0 255.255.255.0
set gateway 192.168.3.2
set device "port2"
set comment "TO_VLAN200"
next
end
- As you can see below, I can ping both the VLANS and internet as well.
Fortigate-FW # execute ping 192.168.100.2
PING 192.168.100.2 (192.168.100.2): 56 data bytes
64 bytes from 192.168.100.2: icmp_seq=0 ttl=127 time=2.3 ms
64 bytes from 192.168.100.2: icmp_seq=1 ttl=127 time=1.0 ms
^C
--- 192.168.100.2 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 1.0/1.6/2.3 ms
Fortigate-FW # execute ping 192.168.200.2
PING 192.168.200.2 (192.168.200.2): 56 data bytes
64 bytes from 192.168.200.2: icmp_seq=0 ttl=254 time=1.0 ms
64 bytes from 192.168.200.2: icmp_seq=1 ttl=254 time=1.0 ms
^C
--- 192.168.200.2 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 1.0/1.0/1.0 ms
Fortigate-FW # execute ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
64 bytes from 8.8.8.8: icmp_seq=0 ttl=127 time=295.3 ms
64 bytes from 8.8.8.8: icmp_seq=1 ttl=127 time=261.9 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=127 time=256.3 ms
^C
--- 8.8.8.8 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 256.3/271.1/295.3 ms
- Let's configure Fortigate to allow traffic only from VLAN 100 to the internet
- In order to achieve this we need to create an address object and a Policy, by default all the traffic is denied from any to any. I am trying to ping internet from my lan PC but it's not pinging because no policy on the FW
config firewall address
edit "VLAN-100"
set uuid 0a162190-eee6-51ed-cf39-2e97ebcc3967
set comment "VLAN_100_NETWORK"
set subnet 192.168.100.0 255.255.255.0
next
end
- Configuring a policy and I am allowing opening all the service ports in the policy but you can open as per the requirement
config firewall policy
edit 1
set name "VLAN100_TO_INTERNET"
set srcintf "port2"
set dstintf "port3"
set action accept
set srcaddr "VLAN-100"
set dstaddr "all"
set schedule "always"
set service "ALL"
set logtraffic all
set logtraffic-start enable
set comments "Created by Dinesh for testing"
next
end
- Testing Traffic Flow
- I can access from my VLAN 100 pc. Congratulation if you are follwing the lab then you will achieve this milestone.
- We can see firewll is having the hits and working perfectly fine.
- Navigate to Logs & Report to see the logs
Fortigate-FW # diagnose sniffer packet port2 none 1 20
Using Original Sniffing Mode
interfaces=[port2]
filters=[none]
1.621218 192.168.100.2.56682 -> 4.2.2.2.53: udp 28
1.937322 4.2.2.2.53 -> 192.168.100.2.56682: udp 44
1.943106 192.168.100.2 -> 142.251.39.110: icmp: echo request
2.245814 142.251.39.110 -> 192.168.100.2: icmp: echo reply
2.942900 192.168.100.2 -> 142.251.39.110: icmp: echo request
3.257274 142.251.39.110 -> 192.168.100.2: icmp: echo reply
3.950927 192.168.100.2 -> 142.251.39.110: icmp: echo request
4.263038 142.251.39.110 -> 192.168.100.2: icmp: echo reply
4.477100 192.168.100.2.54520 -> 4.2.2.2.53: udp 32
4.779473 4.2.2.2.53 -> 192.168.100.2.54520: udp 48
4.781009 192.168.100.2.49362 -> 142.250.179.100.443: syn 3104154528
4.781193 192.168.100.2.49363 -> 142.250.179.100.443: syn 3751954507
4.781723 192.168.100.2.49364 -> 142.250.179.100.443: syn 3245179220
4.782329 192.168.100.2.49365 -> 142.250.179.100.443: syn 3815445466
4.782500 192.168.100.2.49366 -> 142.250.179.100.443: syn 3213634623
4.783049 192.168.100.2.49367 -> 142.250.179.100.443: syn 2598285052
4.963304 192.168.100.2 -> 142.251.39.110: icmp: echo request
5.079899 142.250.179.100.443 -> 192.168.100.2.49362: syn 1522942622 ack 3104154529
5.080893 192.168.100.2.49362 -> 142.250.179.100.443: ack 1522942623
5.081772 192.168.100.2.49362 -> 142.250.179.100.443: psh 3104154529 ack 1522942623
- How to take fortigate backup
- Backup configuration file can allow you to restore it into earler version as well.
Login to FW web-ui http://192.168.47.10 and navigate to admin >> Configuration >> Backup
there you have to download in the local pc or to take it into usb disk and the backup can be encraypted if you select encryption option.
once you click on ok, you will see one .conf file is getting downloaded
That's all guys, Thank you for patience and I hope you will be able to do the same. Do Labbbbiiiiiiiiing
I hope
this has been informative for you. If it seems helpful then Like, Share and
Don’t forget to subscribe and follow me for the upcoming posts
https://www.youtube.com/channel/UC0-p23p1xWsZsTXHUQ7CiJg
https://www.facebook.com/networkinginfo/
https://twitter.com/Dj1Pali
https://www.instagram.com/a_bhartiya_rider/
https://www.linkedin.com/in/dinesh-jangid-515b6a23/


.JPG)








Post a Comment